If you spend any amount of time with technology or security, from the enthusiast level to the enterprise level, you will come across benchmarks and best practices. Not only is it good to know things are working as intended, it’s also a good idea to compare your results with others, so that you can be sure everything is optimized. One solution for checking against best practices is the 20 CIS Controls list.
I previously wrote about CIS by talking about one of their ISACs, their MS-ISAC program to be more specific. They have multiple suites of cyber security products and solutions available for organizations big and small – mostly for government agencies and school systems.
Table of Contents
What Is CIS?
The Center for Internet Security, Inc. (CIS) is a 501(c)(3) nonprofit organization whose mission is to (1) identify, develop, validate, promote, and sustain best practices in cyber security; (2) deliver world-class cyber security solutions to prevent and rapidly respond to cyber incidents; and (3) build and lead communities to enable an environment of trust in cyberspace.
Source: CIS About Us
Why Use Their Security Controls?
The 20 CIS Controls are a relatively small number of prioritized, well-vetted, and supported security actions that organizations can take to assess and improve their current security state. They also change the discussion from “What should my enterprise do?” to “What should we ALL be doing?” to improve security across a broad scale.
But this is not a one-size-fits-all solution, in either content or priority. You must still understand what is critical to your business, data, systems, networks, and infrastructures, and you must consider the adversarial actions that could impact your ability to be successful in the business or operation. Even a relatively small number of Controls cannot be executed all at once, so you will need to develop a plan for assessment, implementation, and process management.
Source: CIS Best Practices (Controls)
Security Control List
You need to signup to access their downloads, as that’s part of their license agreement to use the materials. Once you do, there are 3 main docs to explore:
- XLSX (Excel) Spreadsheet that lays out the 20 CIS Controls and implementation plan
- PDF explaining the 20 CIS Controls
- PDF explaining the top 5 CIS Controls (Basic controls in the group plan)
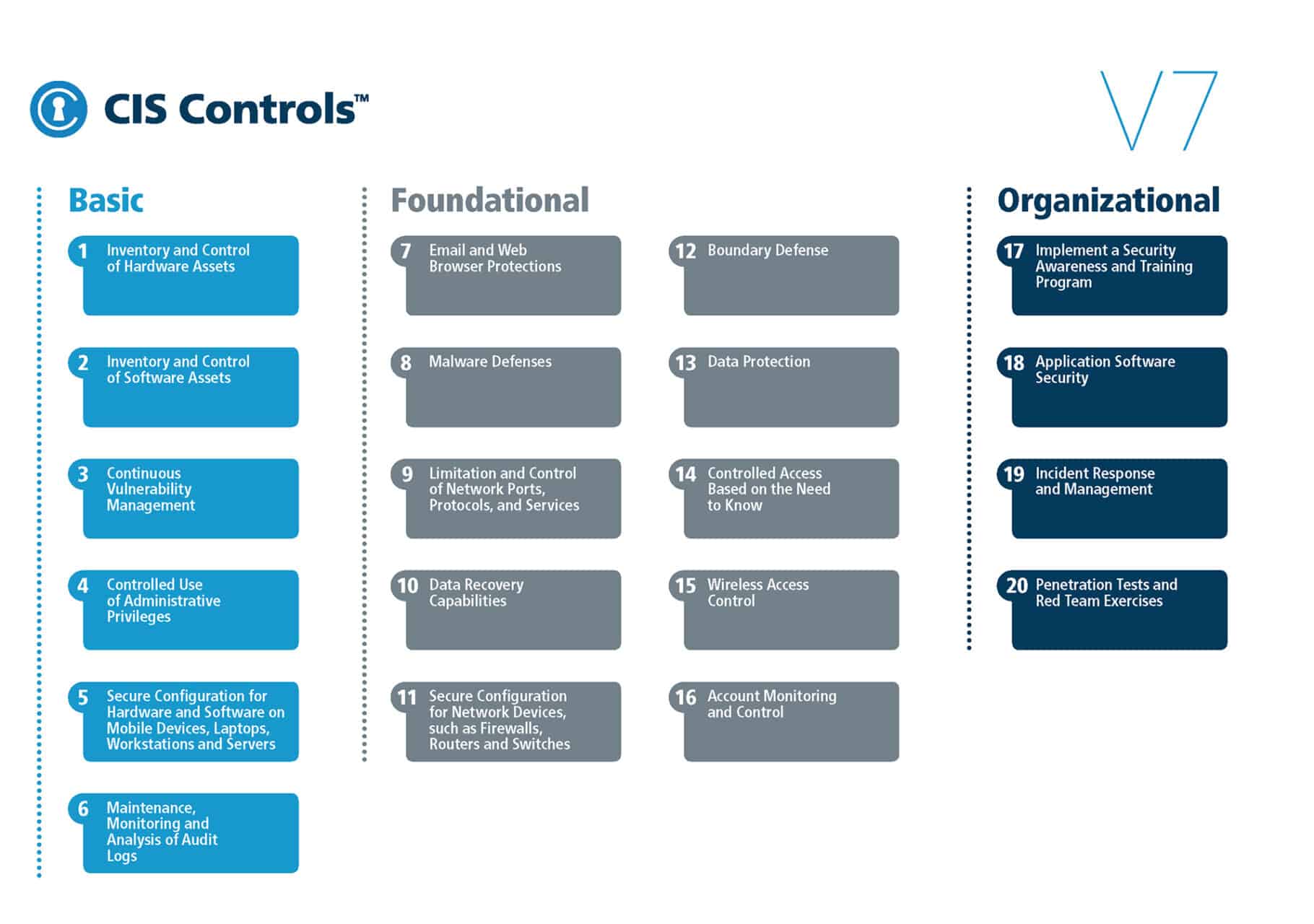
Here’s the full list of the 20 CIS Controls. Think of the full list like the table of contents. You can either go to that table of contents or go straight to the control you’re looking for by checking out the links below.
Basic CIS Controls
- Inventory and Control of Hardware Assets
- Inventory and Control of Software Assets
- Continuous Vulnerability Management
- Secure Configuration of Enterprise Assets and Software (Previously Controlled Use of Administrative Privileges)
- Secure Configuration for Hardware and Software on Mobile Devices, Laptops, Workstations and Servers
- Maintenance, Monitoring and Analysis of Audit Logs
Note: Following through with the top five here in the Basic category can allow for a prevention of incoming attacks by 85% (research based on Verizon DBIR 2017 report). The bad guys use attacks that scale. Now you can defend at scale by using this prioritized list of actions. Fans of the Pareto 80/20 Principle will resonate most with this.
Foundational CIS Controls
- Email and Web Browser Protections
- Malware Defenses
- Limitation and Control of Network Ports, Protocols and Services
- Data Recovery Capabilities
- Secure Configuration for Network Devices, such as Firewalls, Routers and Switches
- Boundary Defense
- Data Protection
- Controlled Access Based on the Need to Know
- Wireless Access Control
- Account Monitoring and Control
Organizational CIS Controls
- Implement a Security Awareness and Training Program
- Application Software Security
- Incident Response and Management
- Penetration Tests and Red Team Exercises
Note: What type of attack prevention do you get for implementing all 20 security controls? Try roughly 97% prevention of the most common cyber attacks. Not bad. This shows a good lesson in the balance of defense in depth and diminishing returns.







